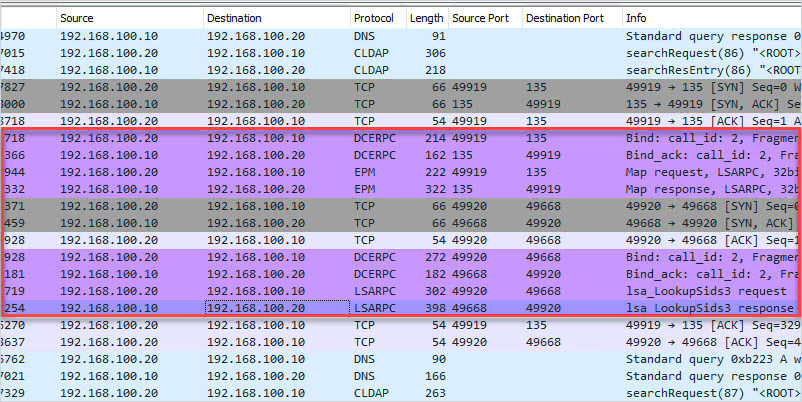
![Cisco UCS Director Installation Guide for VMware vSphere and Microsoft Hyper-V, Release 6.8 - Ports [Cisco UCS Director] - Cisco Cisco UCS Director Installation Guide for VMware vSphere and Microsoft Hyper-V, Release 6.8 - Ports [Cisco UCS Director] - Cisco](https://www.cisco.com/content/dam/en/us/td/i/300001-400000/300001-310000/305001-306000/306000.jpg)
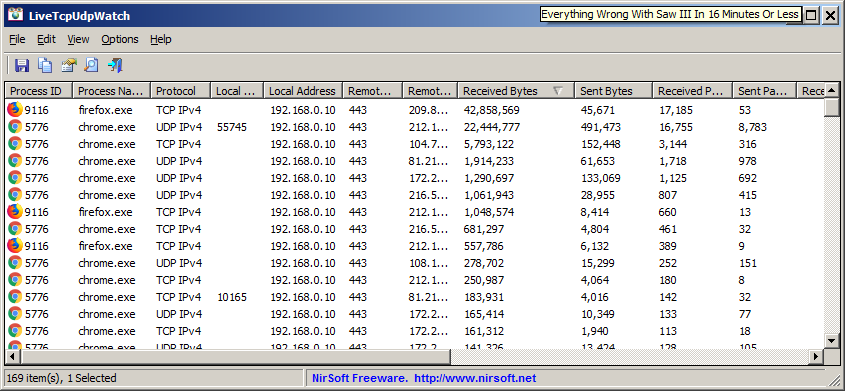
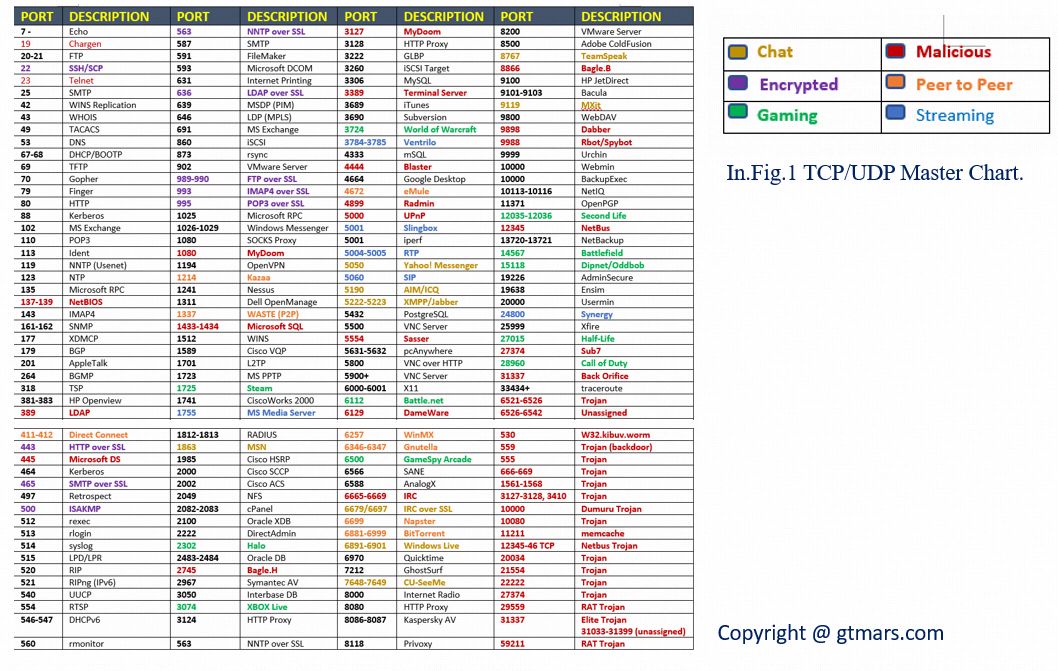
Cisco UCS Director Installation Guide for VMware vSphere and Microsoft Hyper-V, Release 6.8 - Ports [Cisco UCS Director] - Cisco
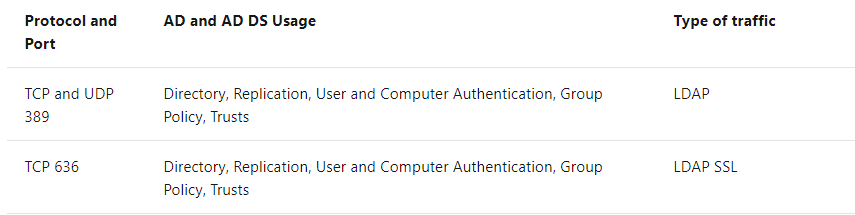
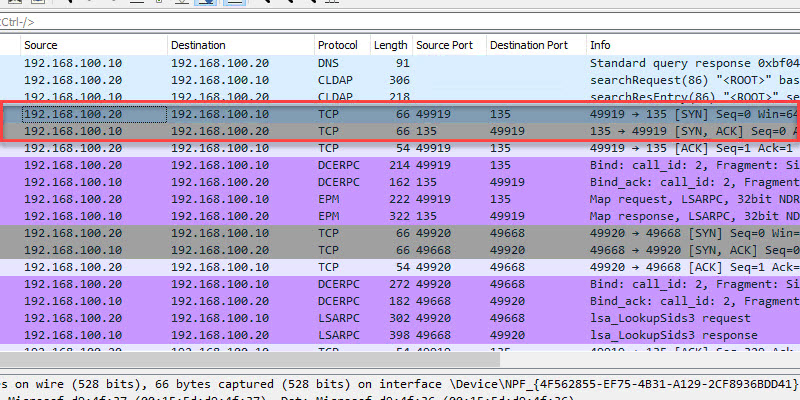
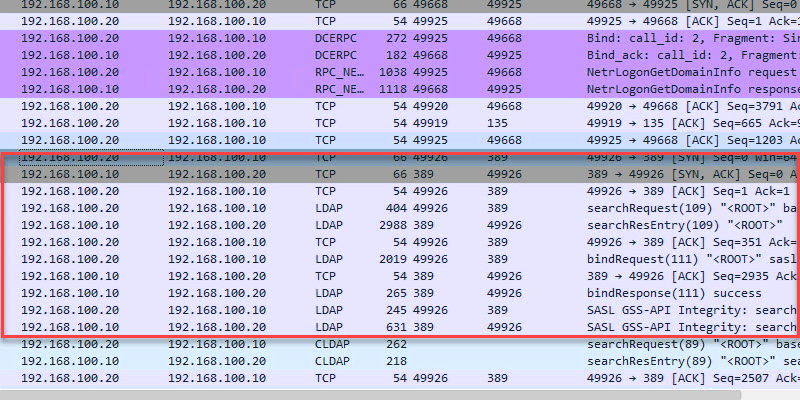
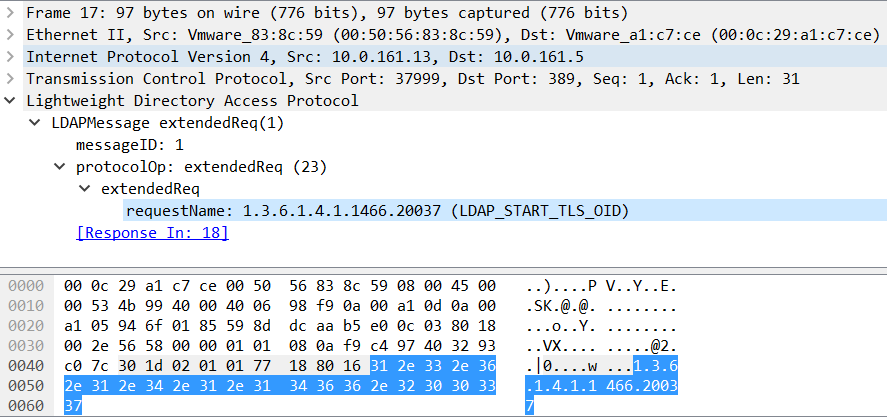
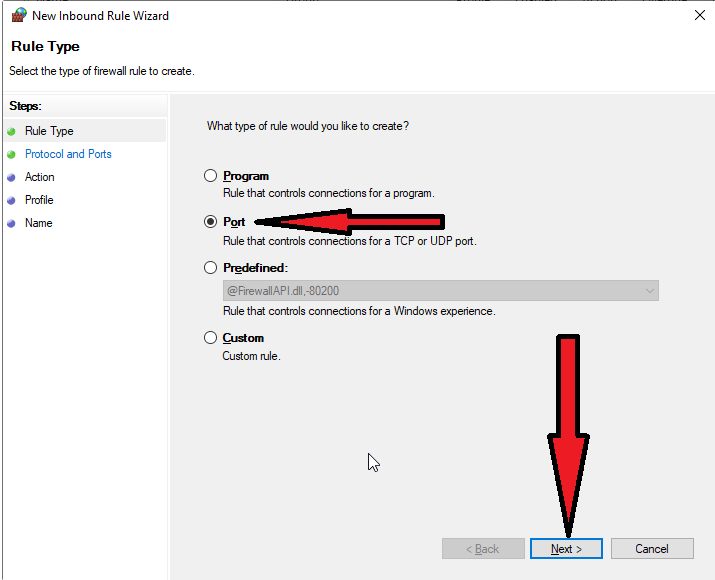
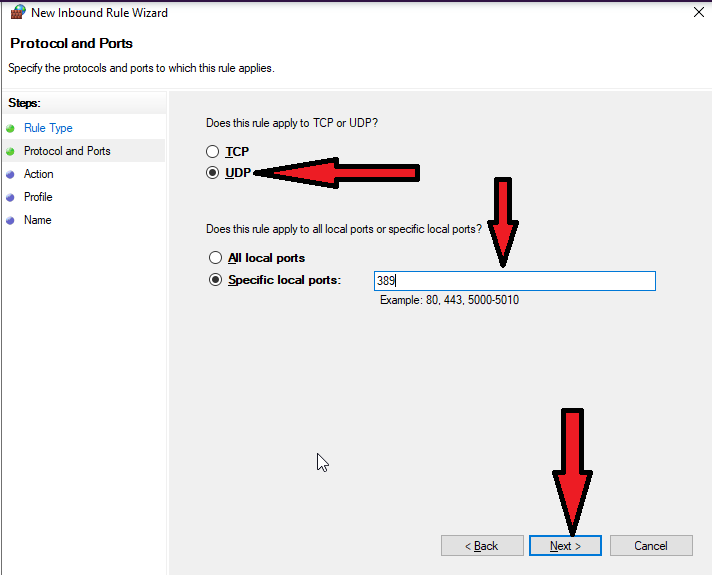
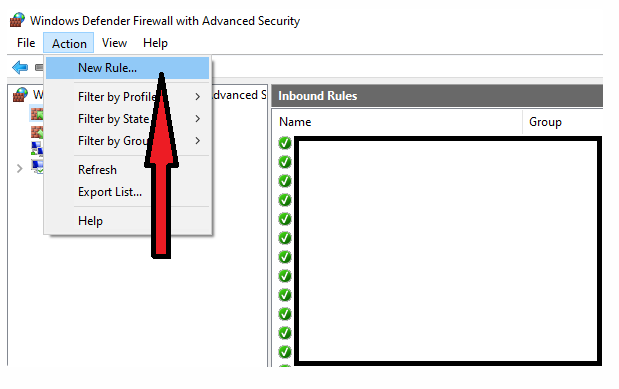
Is port 389 on AD in anyway used or required when a new client queries via secure LDAP? - Microsoft Q&A
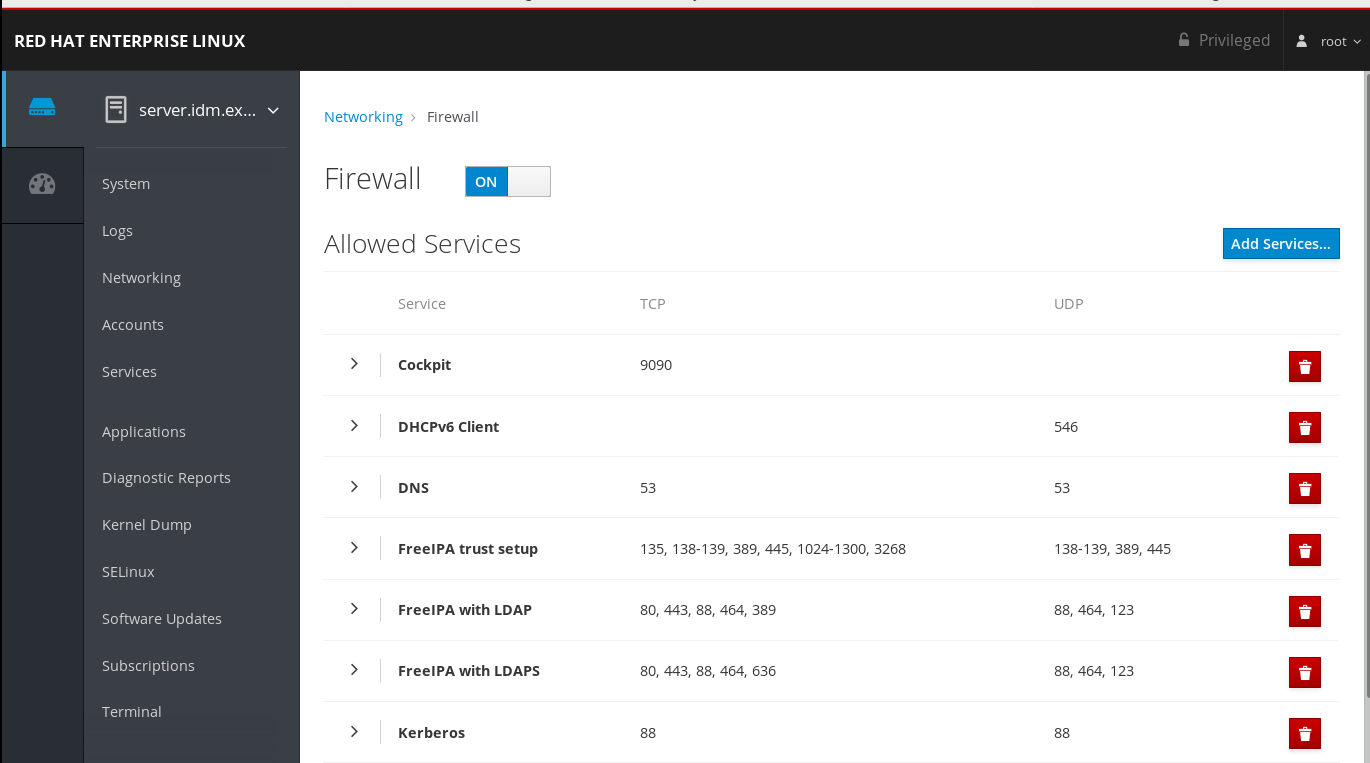
Chapter 6. Ports required for communication between IdM and AD Red Hat Enterprise Linux 9 | Red Hat Customer Portal