Springboot Java Demo - reloads rotated secrets without restarting by secrets provider for k8s as cronjob · Issue #21 · cyberark/conjur-template · GitHub
How To Secure Secrets Within Your Java Application With an Open Source Secrets Management SDK - Conjur
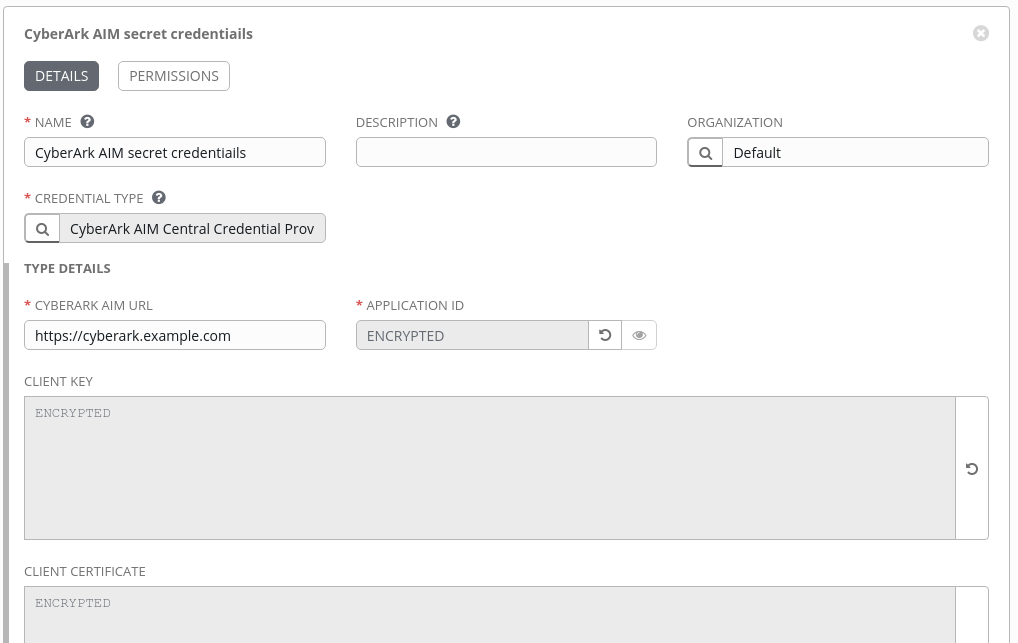
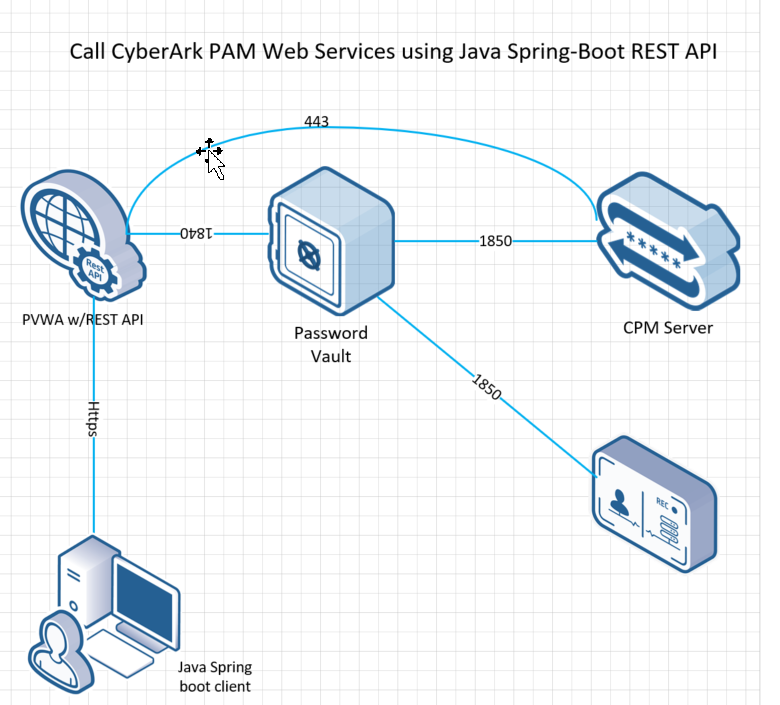
![CyberArk Tutorial | For Beginners [ STEP-IN ] CyberArk Tutorial | For Beginners [ STEP-IN ]](https://www.acte.in/wp-content/uploads/2022/01/CyberArk-Tutorial-ACTE.jpg)