International Summer School on Information and System Security Stack Based Buffer Overflows Alberto Ornaghi Lorenzo Cavallaro. - ppt download
assembly - Why did Intel chose 90h machine code for their NOP instruction instead of a 0? - Reverse Engineering Stack Exchange

A complete tutorial on the stack-based buffer overflow programming using C code on Linux opensource OS with real demonstration
How is a jump instruction used as a no-operation (NOP) opcode on certain CPUs such as the ARM architecture? - Quora



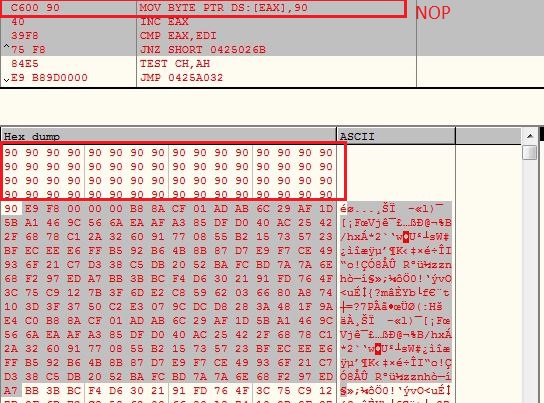
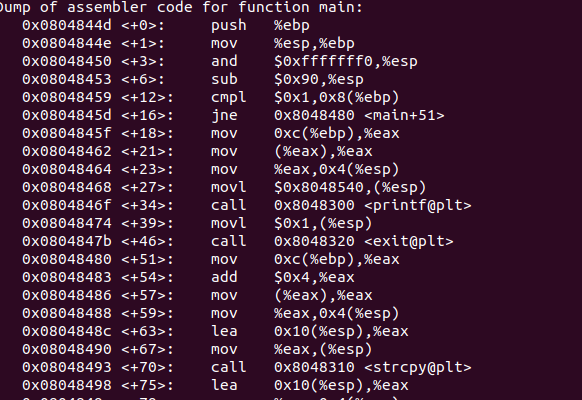



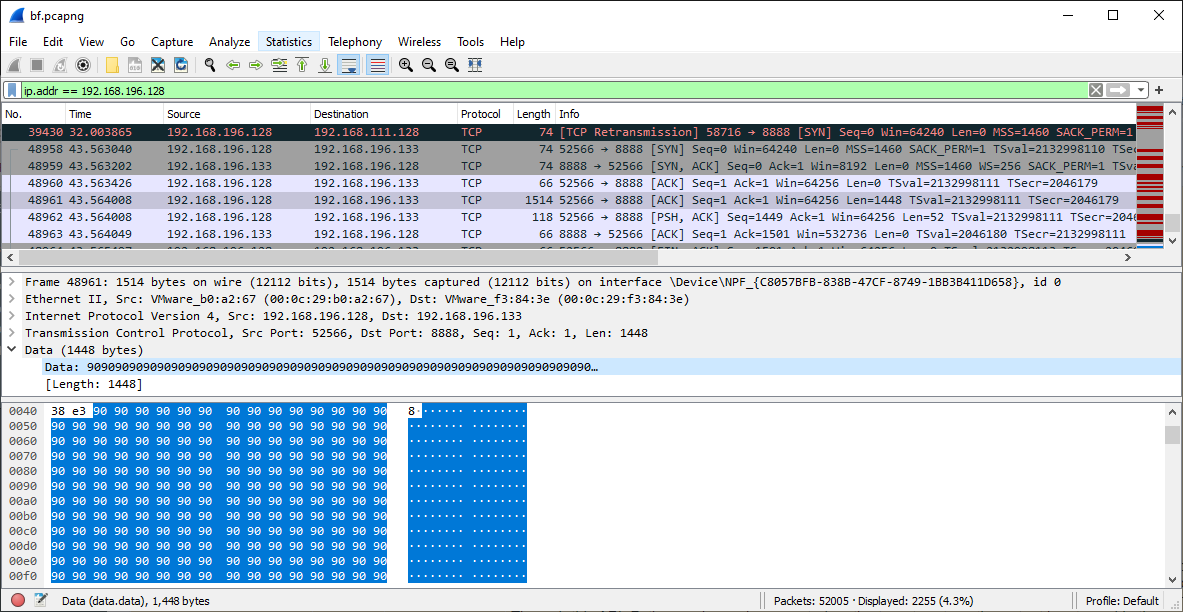



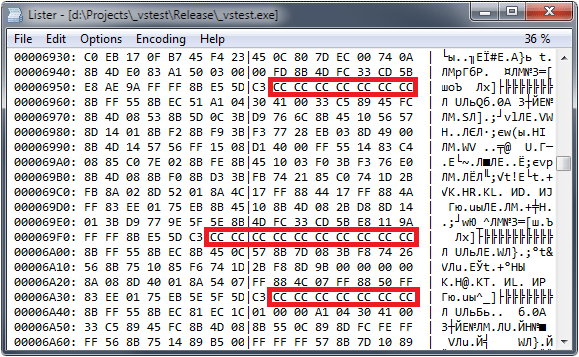

![NOP Sleds - Practical Malware Analysis [Book] NOP Sleds - Practical Malware Analysis [Book]](https://www.oreilly.com/api/v2/epubs/9781593272906/files/httpatomoreillycomsourcenostarchimages2150985.png.jpg)